FIGURE 1.1: SHARING A PRINTER IN A NETWORK
Table of contents
The purpose of this chapter is to provide an introduction to the technology and business use of computer networks. It introduces some of the concepts fundamental to the operation of computer networks. These concepts are essential to an understanding of the workings of computer networks, and form the foundation on which a more complete understanding will be built in following chapters. The chapter also describes in general terms the basic uses of computer networks. When specialised and combined, these generic uses can be used to create any number of business services and applications.
After this chapter; if you want to know more, read Chapter 1 of James F. Kurose and Keith W. Ross, " Networking: a top-down approach", (6th edn.).
The module begins with an introduction to network technology. This chapter starts by considering the reasons for attaching a computer to a network, and underlines them by comparing and contrasting the capabilities of a stand-alone computer and a networked computer. Various ways in which a computer may be attached to a network are described before going on to consider, in an introductory fashion, some of the different types of computer networks. The networks described range from small, local area networks to the Internet, with its global coverage. The roles of hardware and software in the creation of a computer network are described, and their interaction and interdependence are stressed.
In view of the fact that computing devices (including computers, smartphones, etc) of any kind may be attached to a network, the need to establish some kind of uniformity of network operation is explained, and the way in which this is imposed by means of standard ways of operating is described.
In addition, this chapter introduces, or revisits as the case may be, some basic ideas on binary representation, data, coding and files.
A computer network is a network that interconnects computing devices. The reason for attaching a device to a network is to connect it to the other devices that are already attached to the network. At the same time, the user of the device is, in effect, connected to the users of other devices. The benefits that stem from this connectivity are that a devices can:
communicate with other devices, and
share resources with other devices
These capabilities are made available in the form of services. Computer networks can offer a range of communication services. Examples of services offered include:
Electronic mail (email): Provides the users of computers with a fast mail-like service.
Social chat: Provides users with the ability to exchange short texts, pictures, audio and video in real time. Examples of Internet applications offering such services include Facebook, Twitter, Skype and WhatsApp.
E-commerce: Provides users with the ability to conduct business online. Companies such as Amazon and Alibaba provide the services to users to purchase and sell items online.
Before continuing, you could pause to consider what kind of resources might be shared by the computers on a computer network. The resources that can be shared include:
information
advice
software
computing facilities
storage
printers
These items can be broadly classified as software and hardware. The software category includes information, expertise, software and, broadly, anything that can be stored in digital form in a file. The hardware category includes the computer hardware, probably to be used for computing, and computer peripherals, including storage devices to be used for storage. A service is usually provided for sharing software and another for sharing hardware. Since most software items can be stored in a file, the service for sharing them usually takes the form of a file transfer service.
Example: The illustrated network segment in Figure 1.1 below contains three computers and one printer. All the computers in a network share one printer for all printing jobs.

FIGURE 1.1: SHARING A PRINTER IN A NETWORK
A computer network is made up of software and hardware.
Hardware is needed to create the physical network - to connect the computers, and to provide the communication channels/medium of the network. Figure 1.2 below illustrates some of the hardware used in making a computer network.
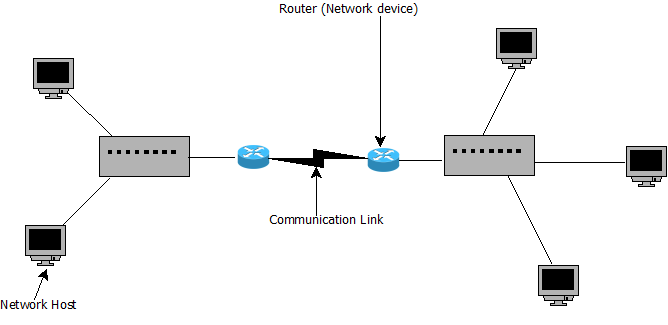
FIGURE 1.2: COMPUTER NETWORK HARDWARE
Hosts: A host is a device used to connect to the network. This can be computers, laptops, smartphones, tablets, TVs, gaming consoles, etc.
Communication links and network devices: Hosts are connected together using communication links and network devices. Communication links are made up of different types of physical media, copper wires, coaxial cable, radio spectrum and optical fibre. Network devices take incoming network messages from one communication link and switch them to another communication link. There are different types of devices in the network, with the common types being routers and switches.
Network software is needed to provide the necessary network services to make this hardware:
usable,
reliable, and
transparent
Application software is needed to support different types of communication and resource sharing. The application software provides the services that will be available over this communication network. The application software in this environment is said to be distributed, since the application is installed on multiple devices that exchange data with each other.
There are different types of computer networks. Computer networks can be categorised by their size or their purpose. In this section, we will discuss different types of computer networks characterised by size.
LAN is devised to meet the needs of a small group of people in the same location, consisting of a communication link to which all the computers can be attached. An example of LAN is a network at UCT upper campus.
When all the computers on the network are carrying out similar tasks or are used by the members of the group to achieve some overall task, it is useful to have a computer on the network to hold the shared resources or to store the results of co-operative efforts. Such a computer is called a server and, for the moment, we can think of a server simply as a computer that holds resources needed by other computers. There is also the issue of how a number of computers can share one communication link, but that is a topic for a subsequent chapter.
WAN covers a large area. A well-known example of WAN is the Internet.
The Internet, of course, provides global connectivity. It does this by linking together other networks such as networks belonging to organisations, national data networks and so on. The internet connects traditional desktop PCs, workstations, computer servers, laptops, smartphones, tablets, TVs, gaming consoles, automobiles and sensing devices throughout the world. Home computers connect to the internet through the Internet Service Provider (ISP). ISPs provides a wide range of types of network access to computers, including;
Digital Subscriber Line (DSL): Computers connect to the ISP using an existing telephone line as shown in Figure 1.3. Most homes have telephone copper wires already installed. To make a computer use an existing telephone line for Internet connection, a DSL modem must be connected to a computer and the telephone line. The DSL modem converts digital data from a computer to analogue data to be transmitted over the copper telephone wires. On the ISP end, a Digital Subscriber Line Access Multiplexer (DSLAM) converts the analogue signal back to digital. The data transmitted over the telephone line is encoded at a different frequency from that of the traditional telephone signal. This allows simultaneous transmission of data and telephone signals.
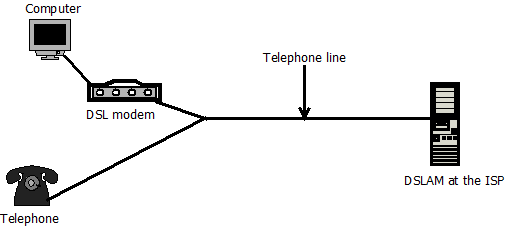
FIGURE 1.3: DSL INTERNET ACCESS
> **Cable**: Unlike DSL, cable Internet uses existing home television cables.
> Like DSL, computers need cable modems to connect to television cables. The
> cable modem converts digital data to analogue signals. On the ISP end, a
> cable modem termination system (CMTS) converts the analogue signal back to
> digital. One feature that makes cable Internet different from DSL is that
> all homes connected to the same television cable share the same broadcast
> medium.
> **Fibre**: This type of network access provides a high-speed fibre cable
> from the ISP directly to the home. A fibre cable uses glass (or plastic) to
> transmit data as a lightwave. A fibre cable can reach transmission rates of
> up to 43 terabits per second.A network's architecture or topology is essentially the arrangement of various network elements. In a good architecture, hardware and software will be well matched to each other. The rest of this section shows how the structure of the hardware and the operation of the software of a network are inextricably related to each other, so that they cannot sensibly be selected individually and without regard for each other.
Consider the ways of linking computers shown in Figure 1.4 below:
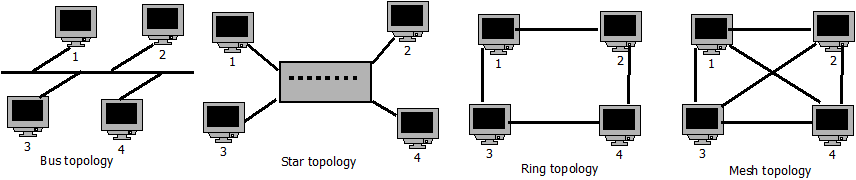
FIGURE 1.4: NETWORK TOPOLOGIES
Bus topology: All computers connect to a single backbone line.
Star topology: All computers connect to a central device called a hub or switch.
Ring topology: Computers are connected in a logical ring. Data moves in a circular way from one computer to another on the network.
Mesh topology: Mesh network is fully connected in that every computer is connected directly to all the others.
Now consider what has to happen when computer 1 needs to send a message to computer 4.
In the star topology, computer 1 sends its message to the central node, which then forwards it to computer 4. In fact, this is the procedure that any two computers must follow to exchange a message.
In the mesh topology, the sending computer selects that connection, linking it to the destination computer, and sends its message directly to its destination.
In a ring topology, computer 1 is not connected directly to computer 4, but it can forward its message to computer 2, which is connected to computer 4 and can, in turn, forward the message to it. The general procedure is that if the sending computer is connected directly to the destination computer it sends its message directly to it; otherwise, it forwards it to a computer that is nearer to the destination computer which, in turn, does the same thing.
In the bus topology, computer 1 puts the message in the backbone line. All the computers connected to the backbone receive the message but only the computer addressed will respond to the message.
The discussion illustrates how the software that determines how a network is to operate - in this case, the rules for routing messages across a network - depends on the topology of the network. The two components of the network architecture must be matched to each other. The consequences of not matching software and network topology can be disastrous (imagine if the routing protocol for the star network were to be used on the mesh network).
Usually, there is a requirement to connect computing devices of any kind to a network. This raises a problem in that different types of devices work in different ways, so that it is not at all clear whether, for example, messages produced by one device and sent to another can be decoded/interpreted the same by the receiving device. To allow devices of different kinds to exchange information meaningfully (that is, in such a way that the information means the same thing to all the devices involved in the exchange), there is a need to enforce some kind of uniformity. This may be achieved by agreeing on a standard way of working to which all devices attached to the same network must conform.
The standards developed to govern hardware and software on a computer network are called network protocols. Network protocols are organised into layers. Each layer can have many protocols, implemented either by software, hardware or both. In the layered architecture, protocols of one layer provide services to the protocols on the layer above. A protocol suite is the definition of the protocols, and the protocol stack is the software implementation of protocols. Many protocol suites have been proposed, but the most popular suites include the ISO OSI reference model and the TCP/IP protocol suite.
The ISO OSI reference model is proposed by the International Organization for Standardization (ISO). It consists of seven layers: application layer, presentation layer, session layer, transport layer, network layer, data link layer, and physical layer, as shown below.
The TCP/IP protocol stack consists of five layers: the application, transport, network, link and physical layers.
Figure 1.5 below shows the ISO OSI and TCP/IP protocol suites. The application layer of the TCP/IP protocol suite has to do the presentation and session-layer services if needed. Otherwise, the functionality of the transport, network, data link and physical layers are virtually similar in both protocol suites.
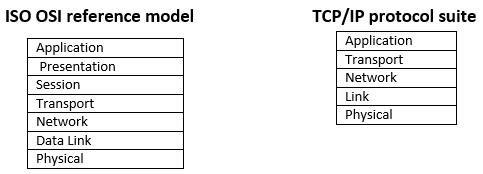
FIGURE 1.5: THE ISO OSI REFERENCE MODEL AND TCP/IP PROTOCOL SUITE
The rest of this section gives a brief explanation of the seven layers of the ISO OSI reference model. More details of each layer will be covered in later chapters.
Protocols that govern the design of network applications are found at the application layer. For example, a web browser like Mozilla Firefox uses the HTTP protocol to transfer documents on the Web from Web servers to the host computer. Other protocols include SMTP (for the transfer of email) and FTP (for the transfer of files between two computers).
The presentation layer provides services that allow communicating applications to interpret the meaning of data exchanged. The presentation layer is responsible for the following:
Data encryption/decryption
Character/string conversion
Data compression
Graphic handling
Data between applications can be communicated in different formats via different sources. Thus, the presentation layer is responsible for integrating all formats into a standard format for efficient and effective communication.
The session layer is responsible for opening, closing and managing a session (semi-permanent dialogue) between two end points. Protocols at this layer include RPC, ADSP and SCP.
The transport layer protocols transport messages between application end points. The popular protocols at the transport layer are TCP and UDP. TCP is connection-oriented, meaning it establishes a connection between two end points before transporting a message. Conversely, UDP is connectionless-oriented. UDP does not guarantee delivery of messages. Transport layer protocols break the long messages from the application layer into shorter messages called segments.
A computer network can have many devices connected to it. For example, the Internet connects hundreds of millions of devices. To send an email from South Africa to Europe, the email will pass through various network devices before reaching its destination. The network-layer protocols are responsible for routing packets through a series of network devices – routers – between the source and destination. When the transport layer passes a data segment down to the network layer, it becomes a network-layer packet known as a datagram. IP protocol is the most popular network-layer protocol.
When the network-layer protocol wants to route a packet from one node to the next node, it passes the packet down to the link-layer protocols, which deliver the packet. Examples of link-layer protocols include Ethernet and WiFi protocols. When the network-layer packet is passed down to the link layer, it becomes a link-layer packet known as a frame.
The responsibility of the physical-layer protocols is to move individual bits in the link-layer frame from one node to another. The protocols in this layer are link-layer dependent.
Computers process data and communication networks transmit data, so we need to be clear about what data is. We can regard it as sequences of 0's and 1's but with the provision that the sequences represent something. For example, they can represent numbers:
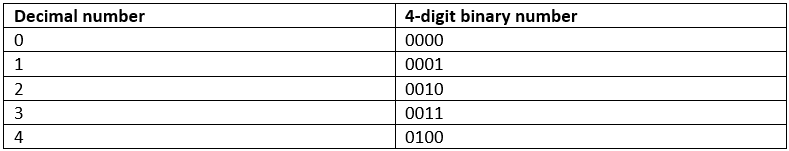
(You should be sure that you can cope with decimal-to-binary and binary-to-decimal conversions.)
They can represent alphanumeric characters. The American Standard Code for Information Exchange (ASCII) is one such representation. Part of this code is:
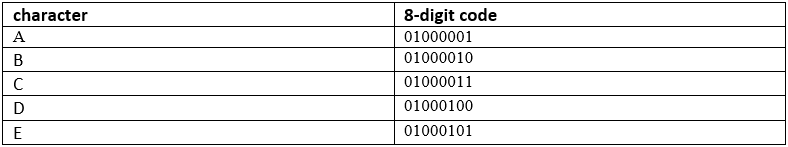
By using this code, a text, such as that of an email, is converted to binary. (You should also find a complete table for the ASCII code in a textbook and familiarise yourself with it. Note that it provides data representations not only for alphabetic characters but also for communication symbols such as ACK and NAK.)
Strings of 0's and 1's can also represent colours (to see this, just replace the capital letters in the table above with the names of colours) or objects in a drawing program, for example (replace the capitals with Line, Rectangle, Oval, etc). Thus, a coloured image can be converted to binary by listing in some defined order the codes for the colours of its pixels. A graphic can be converted to data by listing the codes for the objects that it consists of.
We know that computers store the results of their computations in files. Because just about everything can be represented by a sequence of 0's and 1's, files tend to look much the same whatever their intended meaning. The content of a text file is just a list of the ASCII codes for text symbols, while an image file contains a list of codes for colours. For this reason, it is essential to know what the contents of a file represent before the file can be (properly) used.
A computer network is responsible for transmission of these 1's and 0's from one device to another device.
You can find a discussion of these activities at the end of the chapter.
Activity 1 - How are computers physically attached to a network?
If you have access to a computer that is attached to a local area network, examine the computer to see how it is actually attached to the network. Find the LAN port, or wireless antenna if the computer is connected wirelessly. Has the computer had a card inserted into one of its slots or does it have a built-in network card?
Activity 2 - Computer or network operating system?
On a networked computer to which you have access, check to see if you can find, say, two aspects of the operating system that relate to its use in stand-alone mode and two that relate to its use as a networked machine. Check whether all these aspects are made available in a uniform fashion.
Activity 3 - The players in the network computer arena
Companies most prominent in Network Computer activity have included Cisco. Their attitudes to it have changed quite a lot in a relatively short time. Visit the Cisco site (http://www.cisco.com/) and see if you can find how the company sees the role of the Network Computer currently.
Activity 4 - The ASCII code
Find a table giving the complete ASCII code. Be sure that you can interpret the table correctly - it is often presented in a confusing way. Identify the characters that are intended for communications use only, and compile a precise description of their meanings.
You can find answers/comments for these review questions at the end of the chapter.
Review question 1
You could share the computing facilities on a network by, for example, making use of another computer on the network. Why might you want to do this?
Review question 2
Why would the members of a group want to share information with each other?
Review question 3
How can expertise be shared?
Review question 4
Network services are implemented in software. Where does this software reside?
Review question 5
Is it true that all network applications are distributed?
Review question 6
What does it mean to say that a network is 'transparent' to its users?
Review question 7
Describe in broad terms the architecture of the UCT network and of the Internet.
Review question 8
How many links are there in a network with N computers when they are:
In a mesh topology
In a star topology
Partially connected, with each computer connected to three others
Review question 9
What do the acronyms LAN, MAN and WAN stand for?
Review question 10
More importantly, what are LANs, MANs and WANs?
Review question 11
Using their word processor, someone types the four-letter sequence 'ABCD' twenty-five times and stores the result as a text file. The letters are coded using the ASCII code in which the codes for A, B, C and D are, respectively, by the 8-binary digit representations of the decimal numbers, 65, 66, 67 and 68.
Give the first sixteen binary digits of the data segment of the file.
How many binary digits does the data segment of the file contain?
How long will it take to transmit the data segment of the file across a link operating at 64kbit/sec?
The most significant digit of each code word is transmitted first. In a particular transmission, errors occur to the data in positions 7, 16, 22, 23 and 24. What are the first four characters displayed when the received text file is loaded into a word processor at the receiving computer?
Review question 12
What is an application-layer message? A transport-layer segment? A network-layer datagram? A link-layer frame?
What are some of the differences between the Internet and the World Wide Web (WWW)?
It is well known that, by enabling communication and sharing, the Web encourages the formation of communities. These have been called virtual communities, although there are communities that meet in the real world as well as by using the network. Why does the Web encourage the formation of communities? What is the consequence of this in a business context?
From the points of view of the various interested parties, including users, manufacturers and service providers, what are the relative merits of the networked computer and the Network Computer? Would users be better off with one or the other? Could service providers and network operators give users free Network Computers on the basis that they could find other ways of making money from them? How would they do this? Is it possible that there is a win-win situation for users and providers based on the use of the Network Computer?
The data segment of a file contains nothing but data, and that data will have been assigned a meaning by its originator (it will represent something, whether text or an image or something else). How is it possible to ensure that after a file transfer, the content of the file is interpreted in the way intended by its originator (so that, for example, the contents of a text file are not treated as an image)? Can something be done so that correct interpretation is made automatically?
Computer networks have gone through tremendous evolution in the past decades. Discuss the history of computer networks. ##Answers and Comments
Activity 1
If you have set up your own computer and, for example, attached or installed a modem, you will know how your computer is attached to its network. If you are using a computer that was set up by someone else, look at the sockets at the back or side to see where the cables leading from it are connected. If you have difficulty in locating or identifying the connectors, sockets, cards and so on, then you can seek help from the local technical support staff.
Activity 2
On a stand-alone computer, the operating system provides commands, for example, for examining the contents of a disk and for running a program that is stored on a disk. When a computer is attached to a local area network, the contents of the shared disk drive on the server can be examined in the same way as the contents of a local disk. The network operating system will also allow, for example, examination of the network configuration and identification of other currently active computers on the network.
Activity 3
Generally speaking, Cisco's approach started off with a focus on manufacturing and selling routers. Cisco has expanded well beyond the router market, selling security, wireless caching, Ethernet switches, data-centre infrastructure, video conferencing, and voice-over IP products and services. An examination of the Cisco site should provide a picture of the current situation.
Activity 4
Check out this Website - http://www.asciitable.com/
Review question 1
Perhaps because it's a better computer than yours. Another computer may be able to run a program faster than your computer. It may be able to run a program that your computer cannot run at all because, to give one possible reason, it doesn't have enough memory.
Review question 2
They could be investigating the same topic, in which case sharing the information they have found will prevent them from duplicating each other’s efforts. They could be compiling a joint report, in which case each member of the group needs to see what the others have done.
Review question 3
One way is to communicate with an expert. Another is to access a knowledge base containing expertise that has been elicited from an expert.
Review question 4
Software is, of course, run by computers and, although people speak of the 'software installed on the network', the software is actually installed on the computers on the network.
Review question 5
Yes. If they were not distributed, but ran on one computer, you could run them on a stand-alone computer and there would be no need for a network connection.
Review question 6
That users can, metaphorically, 'see through it'. That is to say that it operates so effectively that users are unaware of its presence in performing any part in an activity they are carrying out.
Review question 7
The Internet is, in effect, one large global network constructed by linking together existing networks with a system of routers. (You can find out what a router is from the glossary or the texts for the module.) The software is the Internet's communications software, TCP/IP. (Again, you can look this up in the same places as you did for a router.)
Review question 8
N*(N-1)/2
N
3*N/2
Review question 9
Local area network, metropolitan area network and wide area network, respectively.
Review question 10
Essentially, they are small-, medium- and large-sized networks, respectively. You should refer to the texts for this module to elaborate on this answer.
Review question 11
0100000101000010
25*4*8 = 800 bits
800/64,000 = 1/80 seconds
CCDD
Repeated vertical stripes of red, blue, green and violet.
Review question 12
Application-layer message: data which an application wants to send and is passed on to the transport layer; transport-layer segment: generated by the transport layer and encapsulates application-layer message with transport-layer header; network-layer datagram: encapsulates transport-layer segment with a network-layer header; link-layer frame: encapsulates network-layer datagram with a link-layer header.